Rejeter la notice
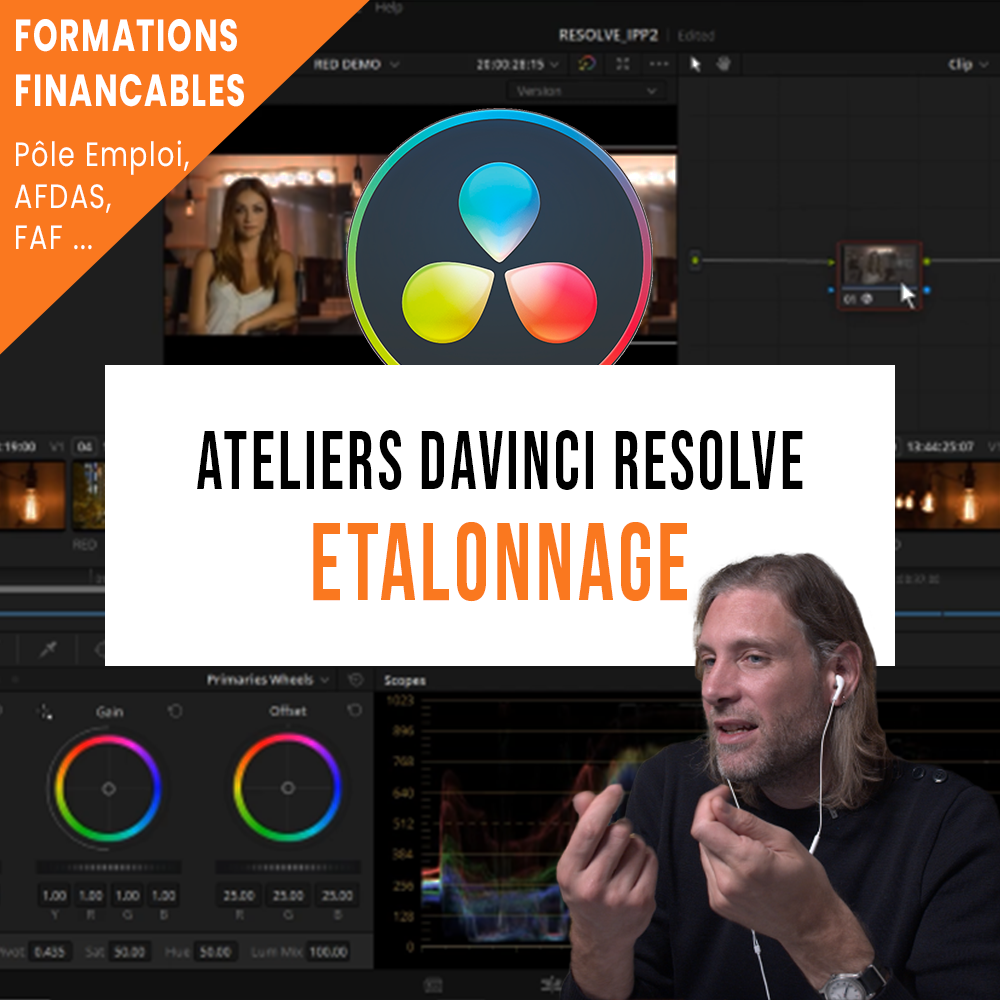
Nos Formations Etalonnage avec Forest reviennent en octobre !
Adoptez une réelle méthodologie d'étalonnage professionnelle et atteignez vos objectifs créatifs avec nos formations intensives sur 3 jours
Toutes les infos
Toutes les infos
Rejeter la notice
 Formation Lumière - Pratique Intensive du 14 au 16 octobre à Paris
Formation Lumière - Pratique Intensive du 14 au 16 octobre à Paris
Formez-vous avec cet atelier de pratique intensive dans des conditions exceptionnelles ! Formation finançable.
Toutes les infos
Redémarrage du PC en connexion internet
Discussion dans 'Informatique et vidéo' créé par Lacer, 12 Août 2003.
Tags:
Page 1 sur 2
Page 1 sur 2
Chargement...
- Discussions similaires - Redémarrage connexion internet
-
- Réponses:
- 8
- Nb. vues:
- 344
-
- Réponses:
- 11
- Nb. vues:
- 314
-
- Réponses:
- 4
- Nb. vues:
- 460
-
- Réponses:
- 6
- Nb. vues:
- 345
-
[CommentFaire?] Quel ordre de connexion SDI 12G
- Réponses:
- 3
- Nb. vues:
- 348